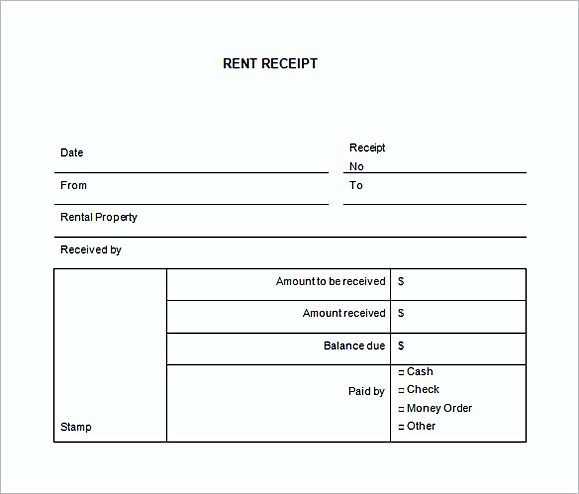
A clear, organized key receipt template simplifies the process of tracking and managing company property. Use this template to ensure each employee acknowledges receipt of keys, locks, and access cards assigned to them. This documentation helps protect against potential loss or misuse of company assets.
Include specific details in the template such as the employee’s name, position, date of receipt, and a list of all keys or access items provided. Make it a standard practice to update this record whenever keys are returned, exchanged, or new items are issued. This will keep all transactions transparent and accountable.
When creating the template, ensure there is space for both the employee’s signature and a witness signature, if applicable. This will strengthen the validity of the receipt and avoid any disputes in the future. Regular audits of key records should be part of your company’s asset management routine.
Creating a Clear Key Assignment Document

Clearly define the key’s purpose, location, and access rights. Specify which areas or systems the key provides entry to, ensuring no ambiguity. State the specific employee assigned to the key, including their name, role, and department. Include a section for the date the key was issued, and a line for the employee’s signature confirming receipt.
Document the return process, outlining the expected timeframe for returning the key when it is no longer needed. Note any penalties for lost or unreturned keys. If applicable, include a designated person or department to contact for key return or replacement procedures.
Maintain a record of each key issued by number or type, and track the status of the key (issued, returned, lost). This allows for quick updates and accountability. Use simple, direct language and avoid jargon to ensure clarity for all employees involved.
Tracking Key Distribution and Returns

Implement a clear system for tracking the distribution and return of keys. Use a dedicated log or database to record each key issued, along with the employee’s name, the date, and the reason for issuance. Include a field for the expected return date and any notes about the key’s condition.
System Setup and Updates
Regularly update the log to reflect key returns and any changes in status. When keys are returned, mark them as received and verify their condition. If a key is not returned on time, send a reminder to the employee and update the log accordingly.
Handling Lost or Damaged Keys

If keys are lost or damaged, promptly assess the situation and determine the necessary actions, such as issuing a replacement or charging the employee for the cost. Document the incident in the log to maintain an accurate record of all key transactions.
Handling Lost or Unreturned Keys

If a key goes missing or is not returned, act quickly. First, inform the relevant team or department about the situation. This helps prevent any security lapses and ensures accountability. Document the incident and request that the employee fill out a form acknowledging the lost or unreturned key.
Next, assess whether the key needs to be replaced or if access control systems can be adjusted temporarily. Replace any locks or security features associated with the key if needed. Depending on company policy, employees may be held responsible for the cost of replacement or additional security measures.
To avoid future issues, establish a clear protocol for key return at the end of each employee’s tenure. Make sure employees understand the consequences of not returning keys on time. Encourage immediate reporting of lost keys and ensure that staff knows who to contact in case of such an event.
Preventive measures: Review the key distribution system and consider implementing a tracking method, such as a log or digital tracking tool. Regular audits can also help identify issues early on and reduce the chances of lost keys.